Collax Security Gateway
Professional security for your network
Professional security for your network
The Collax Security Gateway is a Unified Threat Management (UTM) solution. It combines all security functions in one product. It protects users, the network and your servers from threats from the Internet. It also establishes secure connections to branch offices and mobile users.
Special functions
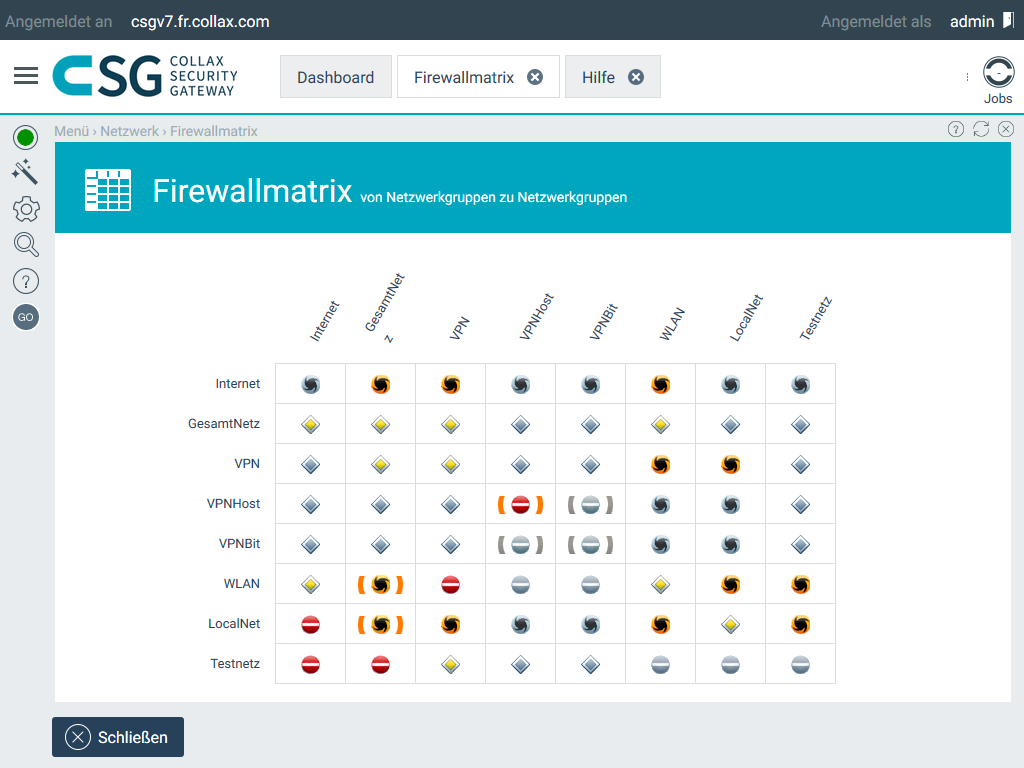
Intelligent firewall and filter technology
In addition to a modern stateful inspection firewall, the Collax Security Gateway provides sophisticated filtering techniques for web and e-mail traffic. Malicious or unwanted data - whether viruses, spam, phishing attacks or malware - are reliably blocked or sorted out. Targeted attacks are reliably fended off.
Remote access and branch networking
VPN (Virtual Private Networking) can be used as a communication channel to securely connect branches and mobile employees to the company’s own network. In addition to the VPN according to the IPsec standard for network connection, the Collax Security Gateway also provides SSL-VPN. SSL-VPN is particularly suitable for the remote access of mobile devices.
Secure e-mail communication
All e-mails are freed from common threats before they are forwarded to the mail server. The mail server is significantly relieved by the defense against viruses and the very high detection rate of spam mails directly at the gateway.
Controlled use of websites
Efficient filters protect against viruses and other malware while surfing. Access to unwanted or illegal content such as extremism, pornography or violence is reliably prevented. Time-controlled usage control for services such as Facebook, YouTube or eBay can regulate which websites employees can access and when.
Network performance and connection reliability
Thanks to the new Collax network link daemon, the software not only reacts faster to changes in network connections, but also evaluates qualitative information - alternative routes or interface connections are established much faster than before and the reliability of existing network connections increases.
The intrusion detection and prevention system
Intrusion detection and prevention (IDS: Intrusion Detection System / IPS: Intrusion Prevention System) provides additional security. The system detects malicious attempts to gain unauthorized access. Attackers can be automatically blocked by the firewall even before they can cause any damage.
Hardened Operating System - Efficient Management
Hardened operating system files of the Collax Security Gateway increase stability and reduce the attack surface for your company. At the same time, the authenticity of the Collax Security Gateway software can be 100% verified (deterministic). All settings can be made easily via a browser-based user interface.
Evaluation and statistics up to the automatically generated configuration report help with the administration of the server. An integration of the server into a network monitoring is possible.
Collax Security Gateway as Appliance
The Collax Security Gateway is also available as an appliance (hardware with pre-installed software). You can find suitable hardware in our distributors.
Further information:
Datasheet: Collax Security Gateway 1079 kB- Reliable enterprise protection through hardened firewall system
- Secure web access for users
- Clean email inboxes through
- Email spam filter
- Includes virus filter for e-mail and web traffic
- Convenient, secure remote access for users
- Optimized traffic policies for your network traffic
- Efficient maintenance and monitoring for administrators
- Modern “Material Design” GUI
Download Live Demo

Collax Server Update 7.2.38 - Security Update and Groupware
Security Update and Collax Groupware Suite

Collax Server Update 7.2.34 - Security Update and Grommunio
Collax Groupware Suite, Let's-Encrypt

Collax Server Update 7.2.34 - Security Update and Document Management
Collax Document Management, Let's-Encrypt, country lock, name resolution

Collax Server Update 7.2.32 - Collax Document Management
New add-on module - Collax Document Management - Now available!
Product downloads
Download 30-day test license
To get a 30-day test license for this product, please complete the form below. After a short while, the license will be sent to the e-mail you specified.
Invalid email address
Download a free one-year license
For private or commercial use
To get a one-year license for the private or commercial use of this product, please complete the form below. If you want to use the license commercially, be sure to specify the name and e-mail address of your company.
A maximum of one free license may be operated simultaneously by a legal or natural person. Pure evaluation and test installations are exempted from this rule.
Upon submission of the form, the download of your ISO file will start automatically. After a short while, the license will be sent to the e-mail you specified.
Invalid email address
References
We want to inspire companies.
We would like to introduce some successful companies and their IT solutions to you here
Hardware compatibility
- Compatibility list 221 kB
Data sheets
How Tos
- Collax Information and Security Intelligence - Setup 45 kB
- Collax Information and Security Intelligence - Reports 452 kB
- Collax Introduction Kibana 406 kB
- Collax IKEv2, L2TP & IPSec VPN How-To 1163 kB
- Collax iOS VPN How-To New for Version 7 388 kB
- Collax E-Mail Archive How-To 174 kB
- Collax Firewall and Security Basics How-To New for Version 7 589 kB
- Collax Firewall und Security Basics How-To 499 kB
- Collax Mailserver How-To 378 kB
- Collax Module Installation How-To 100 kB
- Collax Monitoring with Nagios How-To New for Version 7 305 kB
- Collax Monitoring with Nagios How-To 241 kB
- Collax Networking How-To 78 kB
- Collax PPTP-VPN How-To 317 kB
- Collax Server Setup How-To 43 kB
- Collax Spamfilter How-To New for Version 7 579 kB
- Collax Spamfilter How-To 238 kB
- Collax SSL-VPN How-To New for Version 7 399 kB
- Collax SSL-VPN How-To 240 kB
- Collax VPN How-To 398 kB
- Collax Web Application How-To 206 kB
- Collax Web Security How-To New for Version 7 478 kB
- Collax Web Security How-To 375 kB
- Collax USB installation media How-To 35 kB
- Collax NCP-VPN How-To 1135 kB
- Collax 32bit to 64bit Migration How-To New for Version 7 489 kB
- Collax 32bit to 64bit Migration How-To 602 kB
- Collax Fax Server How-To 414 kB
- Collax Backup How-To 579 kB
- Collax Active Directory How-To 240 kB
- Hardware compatibility list 221 kB
Manuals
Release Notes
- Release Notes CSG 7.2.38
- Release Notes CSG 7.2.34
- Release Notes CSG 7.2.34
- Release Notes CSG 7.2.32
- Release Notes CSG 7.2.30
- Release Notes CSG 7.2.28
- Release Notes CSG 7.2.26
- Release Notes CSG 7.2.24
- Release Notes CSG 7.2.22
- Release Notes CSG 7.2.20
- Release Notes CSG 7.2.10
- Release Notes CSG 7.2.8
- Release Notes CSG 7.2.6
- Release Notes CSG 7.2.4
- Release Notes CSG 7.2.2
- Release Notes CSG 7.1.100
- Release Notes CSG 7.2.0
- Release Notes CSG 7.1.24
- Release Notes CSG 7.1.22
- Release Notes CSG 7.1.20
- Release Notes CSG 7.1.18
- Release Notes CSG 7.1.16
- Release Notes CSG 7.1.14
- Release Notes CSG 7.1.12
- Release Notes CSG 7.1.10
- Release Notes CSG 7.1.8
- Release Notes CSG 7.1.6
- Release Notes CSG 7.1.4
- Release Notes CSG 7.1.2
- Release Notes CSG 7.1.0
- Release Notes CSG 7.0.32
- Release Notes CSG 7.0.30
- Release Notes CSG 7.0.28
- Release Notes CSG 7.0.26
- Release Notes CSG 7.0.24
- Release Notes CSG 7.0.22
- Release Notes CSG 7.0.20
- Release Notes CSG 7.0.18
- Release Notes CSG 7.0.16
- Release Notes CSG 7.0.14
- Release Notes CSG 7.0.12
- Release Notes CSG 7.0.10
- Release Notes CSG 7.0.8
- Release Notes CSG 7.0.6
- Release Notes CSG 7.0.4
- Release Notes CSG 7.0.2
- Release Notes CSG 7.0.0
- Release Notes CSG 5.8.26
- Release Notes CSG 5.8.24
- Release Notes CSG 5.8.22
- Release Notes CSG 5.8.20
- Release Notes CSG 5.8.18
- Release Notes CSG 5.8.16
- Release Notes CSG 5.8.14
- Release Notes CSG 5.8.12
- Release Notes CSG 5.8.10
- Release Notes CSG 5.8.8
- Release Notes CSG 5.8.6
- Release Notes CSG 5.8.4
- Release Notes CSG 5.8.2
- Release Notes CSG 5.8.0
- Release Notes CSG 5.5.18
- Release Notes CSG 5.5.16
- Release Notes CSG 5.5.14
- Release Notes CSG 5.5.12
- Release Notes CSG 5.5.10
- Release Notes CSG 5.5.8
- Release Notes CSG 5.5.6
- Release Notes CSG 5.5.4
- Release Notes CSG 5.5.2
- Release Notes CSG 5.0.34
- Release Notes CSG 5.5.0
- Release Notes CSG 5.0.30
- Release Notes CSG 5.0.28
- Release Notes CSG 5.0.26
- Release Notes CSG 5.0.24
- Release Notes CSG 5.0.22
- Release Notes CSG 5.0.20
- Release Notes CSG 5.0.18
- Release Notes CSG 5.0.16
- Release Notes CSG 5.0.14
- Release Notes CSG 5.0.12
- Release Notes CSG 5.0.10
- Release Notes CSG 5.0.8
- Release Notes CSG 5.0.6
- Release Notes CSG 5.0.4
- Release Notes CSG 5.0.2
Test the Collax Security Gateway 7 right now!
To make it as easy as possible for you to test our security solution, we have set up a demo server version 7 for you. No test licenses or downloads are required. Simply click on the following link and log in with the data given below. You have immediate access to the Collax Security Gateway user interface.
https://demo.collax.com:8001
admin
demo
Do you have any questions?
We would be happy to talk to you. Please use our contact form. We will take care of your request as soon as possible.
Contact us
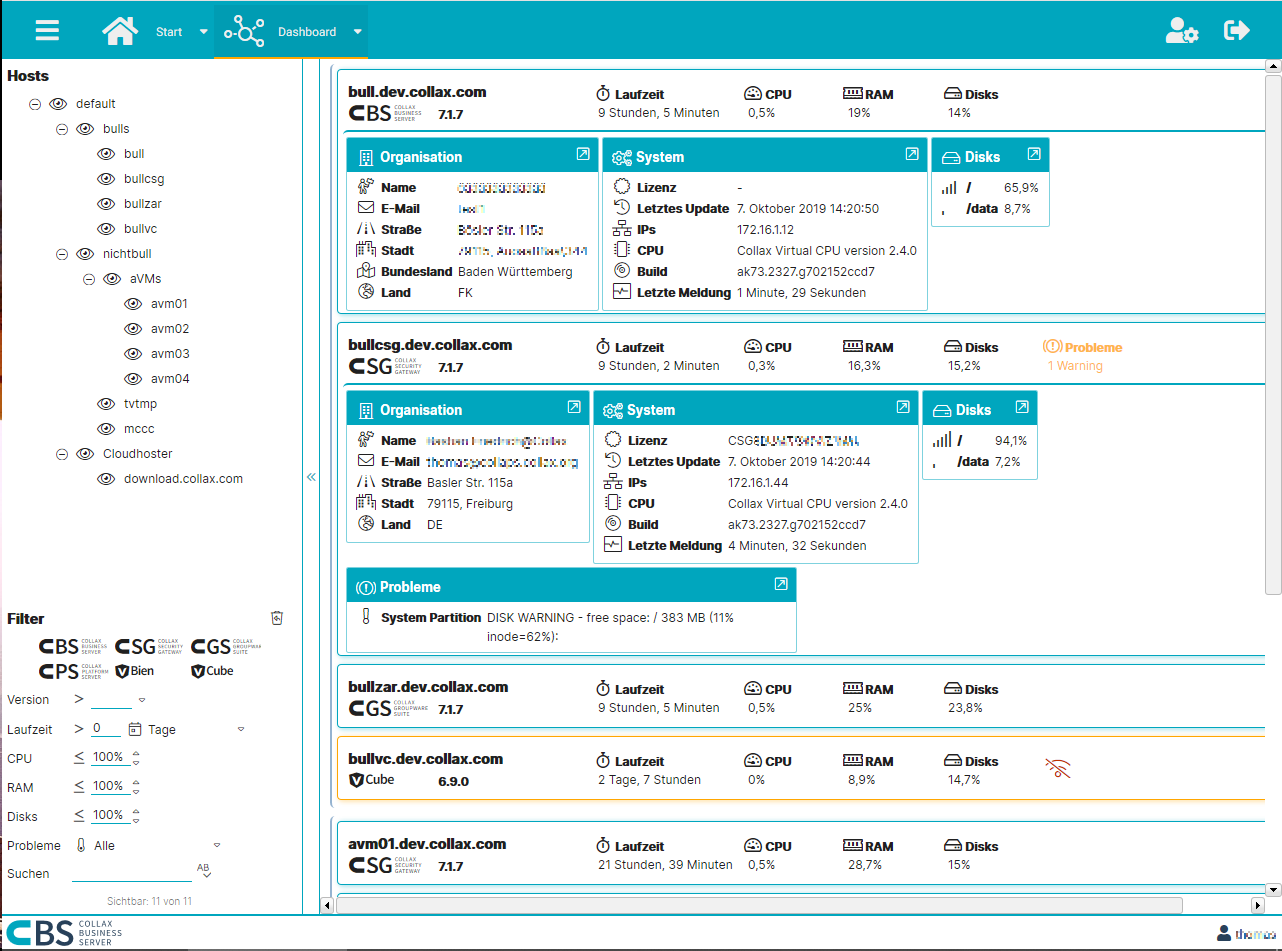
Collax Central
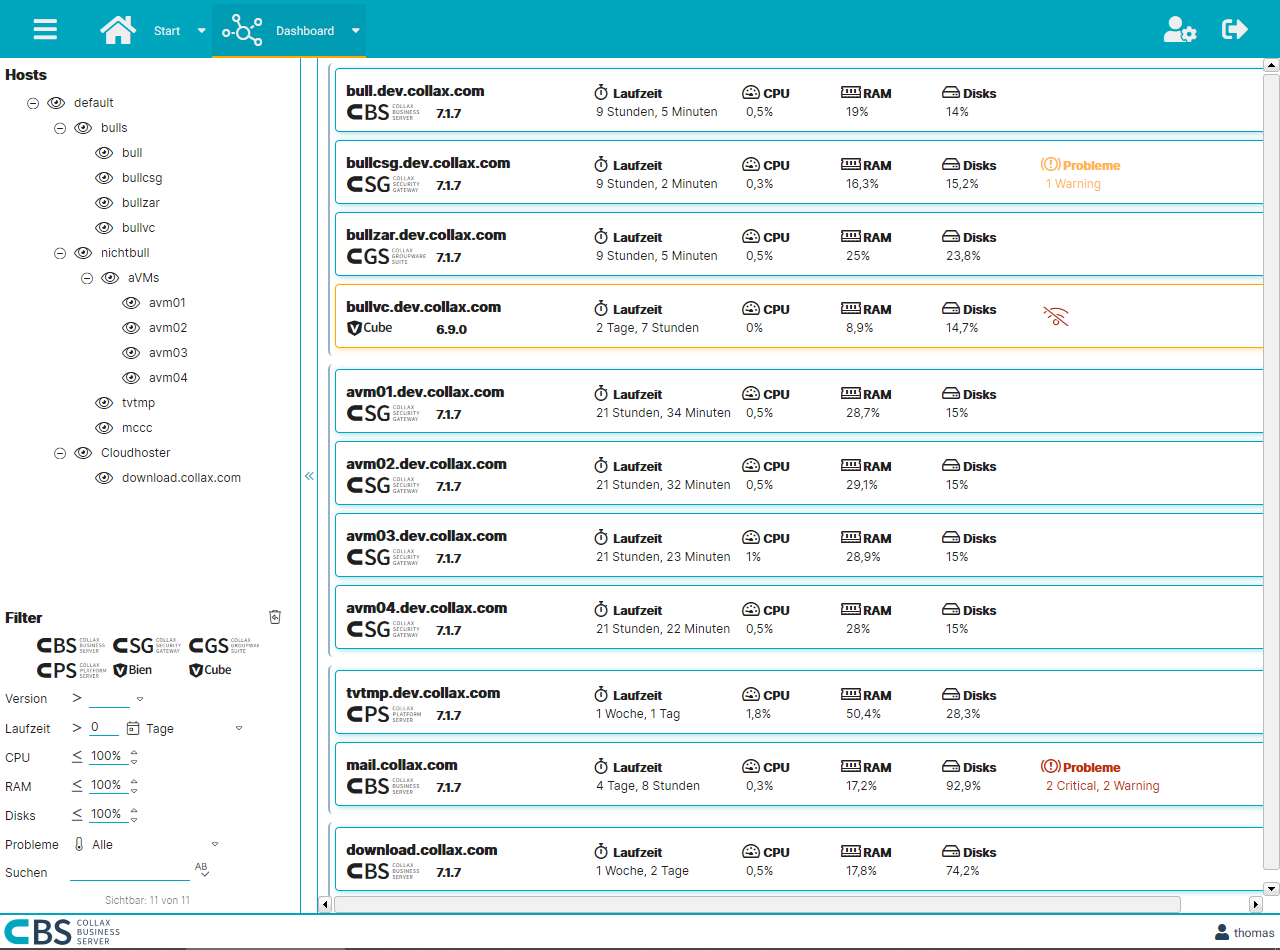
With Collax Central you always have an overview of all Collax servers. This makes administration much easier. Thanks to active system monitoring, Collax Central points out problems at an early stage and offers an effective tool for efficient and fast administration. This is where all the information comes together. This allows problems in a large server landscape to be identified at a glance. Sporadic and regular maintenance tasks are completed quickly.
Always everything in view
The compact overview provides immediate access to all important information on hardware utilization, updates and license terms. Many more detailed information can be displayed with a single click. If maintenance work is due or a problem is detected, a further click is sufficient to perform the administration task.
Hierarchy and structure make the difference
All servers can be sorted into a freely configurable, hierarchical structure. The administrator can create his individual dashboard according to his requirements. Thus he has all information available quickly and clearly. The flexible search function as well as a multitude of filters complete the range of functions.
Collax Avira AntiVir
Collax Avira AntiVir is a high-quality and reliable product for protection against viruses and other malware. It is based on the technology of the market-leading anti-virus company Avira.
Collax has perfectly adapted the award-winning and widely used anti-virus software to the Collax C servers. The solution is seamlessly integrated at the click of a mouse and immediately offers maximum protection against threats from the Internet. Collax Avira AntiVir is based on three different mechanisms: E-mail scanner, file scanner and web traffic scanner.
Collax offers the following variants of the proven anti-virus software:
E-mail Scanner with File Scanner
Installed on the Collax Groupware Suite, the Collax Avira AntiVir extension offers protection against unwanted e-mails and malicious content. We seamlessly integrate Avira’s e-mail scanner and file scanner technology into our servers.
Web Traffic Scanner with File Scanner
In a second variant, we offer the Web Traffic Scanner together with the File Scanner as an extension for the Collax Groupware Suite. This allows you to efficiently and easily control Internet usage within your company. At the same time, the file scanner provides more security by checking data that has been manually brought into the company (e.g. via USB sticks or smartphones).
File Scanner
As a third variant, we only offer the file scanner as an extension to the Collax Groupware Suite. This ensures maximum security for all your data. The file scanner reliably identifies and eliminates infected documents.
- Daemon updates without service interruption
- Administrator alert
- Quarantine for unknown archive formats / file formats
- Automatic deletion of infected files
- Real-time scanning of e-mails (with attachments) and web traffic
- Scan of the file cache
- Supports all popular protocols for file sharing, email, and web
- False Positive Control
Collax Virus Protection powered by Bitdefender
Collax Virus Protection is another solution product that we recommend and offer to protect against viruses. It is aimed specifically at small and medium-sized businesses. The solution uses Bitdefender’s market-leading technology. Installed quickly, it provides triple protection for your business:
E-Mail Scanner
The Email Scanner powered by Bitdefender identifies, analyzes and eliminates unwanted emails with malicious content.
Web Traffic Scanner
The Web Traffic Scanner of Collax Virus Protection allows an efficient and meaningful control of Internet usage. The experience and know-how of Bitdefender combined with Collax are a benefit for the security of your company.
File Scanner
The majority of viruses enter the company manually, e.g. via infected files on USB sticks or smartphones. The infected files are then stored on a file server and can spread throughout the company. With a File Scanner you can identify and eliminate such files. Using the Bitdefender File Scanner on a Collax server allows for accurate localization and efficient scanning technology.
Collax offers all three methods either individually or as a complete package.
- Automatic Updates
- Administrator alert
- Quarantine for unknown archive formats / file formats
- Automatic deletion of infected files
- Scan for all common viruses, Trojans and other malicious software
- Real-time scanning of e-mails (with attachments) and web traffic
- Scan of the file cache
- Supports all popular protocols for file sharing, email, and web
Collax Anti Spam powered by Bitdefender
Collax Anti Spam powered by Bitdefender combines multiple spam and phishing detection technologies to detect and block cyber threats in email traffic. Emails are captured and pass through a variety of blacklists, reputation systems and content filtering technologies to detect spam, phishing, extortion scams and malspam attacks, providing complete email protection for internal users and customers.
High detection rate independent of language and region
The spam filter of Collax Anti Spam is characterized by a high detection rate. The detection rate of the solution is not influenced by language. Collax Anti Spam powered by Bitdefender uses information that does not depend on language or regional characteristics; therefore, it provides the same detection rates for users all over the world.
High throughput, high performance
Collax Anti Spam is specifically designed to ensure high throughput without significantly impacting the performance of your systems … for more efficiency in your business.
Protects email servers and collaboration platforms
Accurate spam filtering removes more than 99.9% of unwanted messages and minimizes false positives. By using powerful anti-spam solutions, productivity losses due to spam and unnecessary technical expenses are avoided.
Not only does inbound spam create costs and risks, but outbound email traffic must also be risk-free to prevent your infrastructure from being misused to send spam and viruses. Otherwise, there is a risk that your IP and domains will be blacklisted.
- Protects email servers and collaboration platforms
- Increased employee productivity
- Better protection through cloud-based technologies
- Low false positive rate
- High throughput, high performance
- Real-time email scanning
Collax Let’s Encrypt
Let’s Encrypt is a certificate authority that offers free X.509 certificates for SSL encryption.
The usual manual procedures are replaced by an automated process simplified. The CA of the Let’s-Encrypt certificates is available for all common Web browsers as a pre-installed, trusted root certificate authority deposited. Thus, browsers do not report warnings or errors for web pages that Encrypt HTTPS with a Let’s-Encrypt certificate Let’s Encrypt Certificates are primarily intended for the encryption of web pages. However, you can use can also be used for other purposes.
The goal of Let’s Encrypt is to enable the setup of an HTTPS server which automatically generates a trusted browser certificate without receives human intervention. This is achieved by executing a Certificate Management Agent on the Web server.
For more information, see also: https://letsencrypt.org/de/
- Validierung und Signierung von X.509-Zertifikaten
- Automatische Bereitstellung eines Browserzertifikats
- Zuverlässige Verschlüsselung von Web-Seiten
- Sichere Domain-Validierung
- TLS-Verschlüsselung mit Let’s-Encrypt-Zertifikaten
Collax SSL-VPN
Today, some information from the company network must also be accessible to external employees at all times. SSL-VPN is the best choice if access is to be quick and easy and security plays an important role. Collax SSL VPN provides functions to connect employees to the company network without installing access software. Only a standard browser is required for access. Thus laptops, tablet PCs or smartphones can be used.
Browser desktop
Via a browser applet it is possible to remote control a shared computer. The workstation from the company becomes mobile - it can be operated effortlessly from on the way or from the home office. You can work with mouse and keyboard as usual. Alternatively, it is possible to use the “Remote Desktop Connection” program available under Windows.
Desktop applications
If access to a specific application on an internal server is necessary or desired, Collax SSL-VPN can establish the required network connection. In order to establish the connection, the user only has to log on via browser. The connection between the application and the server is established in the background. The user can now work as in the office without noticing any difference.
Web applications
Web applications are often used in the internal network that only have a low level of security or can be accessed without user logon. Direct access from the Internet is therefore not possible. Collax SSL-VPN enables secure external access to these applications. After authentication, authorized users can use the application in the usual way.
Security
Each tunnel is protected from access by third parties with modern encryption technology. In addition, the administrator can specify exactly which data is released for which employee and via which type of access.
- Secure access to closed networks
- No installation of clients necessary
- Remote access via any browser
- Assignment of user rights per user
Collax Surf Protection
Time-controlled usage control for web shops, social networks or news sites: Control when your employees can access which websites. Collax Surf Protection is based on Cobion’s sophisticated URL database.
- One of the largest URL databases
- One of the largest image databases
- 68 categories, updated daily
- Up to 150,000 new URLs daily
- Real-time adjustment (Real-Time Monitoring)
- Can be used as blacklist or whitelist