Collax add-on modules
Add-on modules for Collax Server
Collax offers versatile server solutions with individual expansion options. Our customers appreciate this flexibility. The installation of add-on modules is done by downloading corresponding packages from the update server and integrating them into the system.
As a rule, an installation can be carried out as soon as the respective product or add-on module has been activated with a valid licence key.
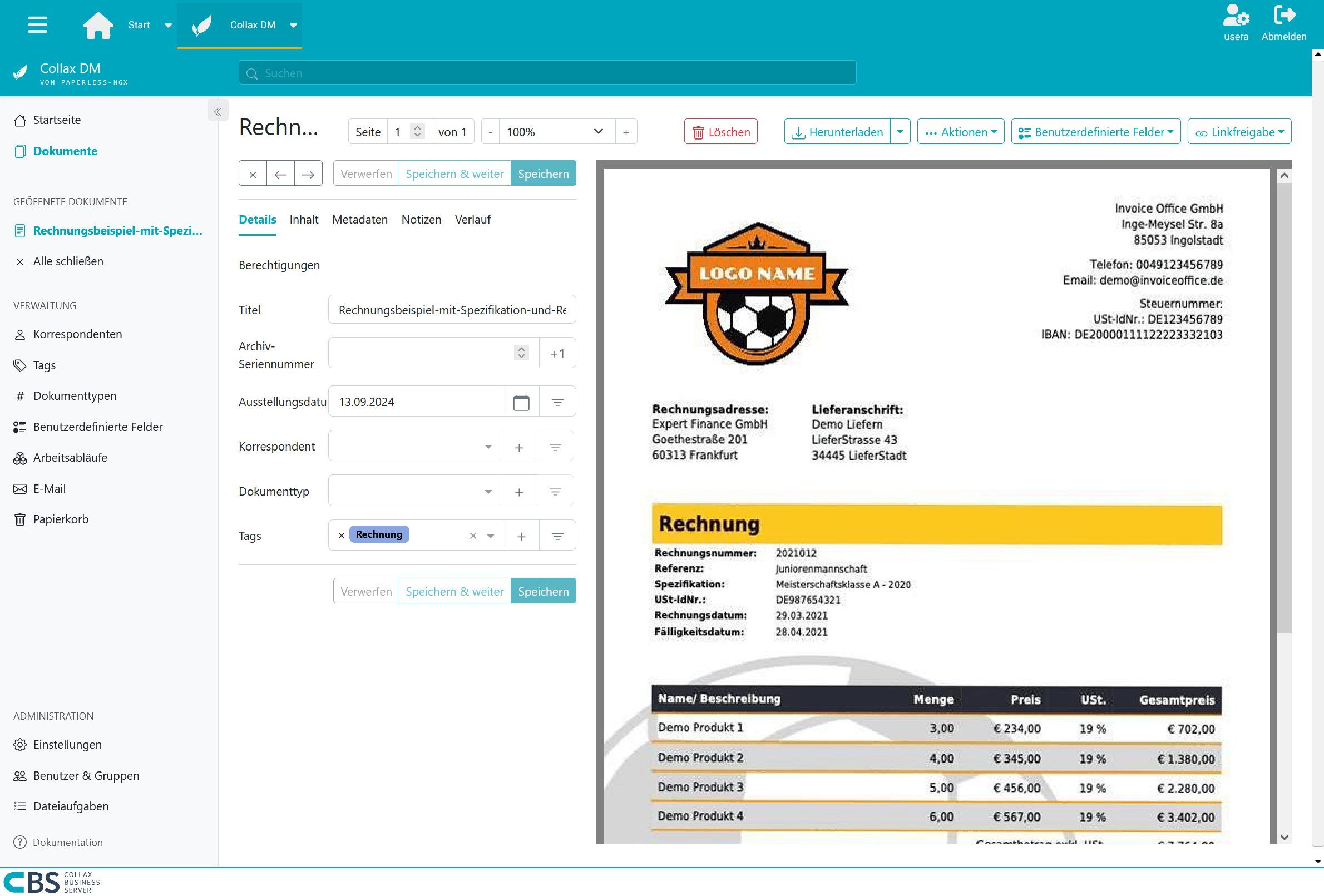
Collax Document Management
Have you ever stood in front of a wall of folders and desperately searched for that one document? Or asked an employee and then had to search for it yourself? In the end it was even filed incorrectly? These are the time thieves that digitalization can save us from.
In an increasingly digital world, it is crucial to find efficient and secure solutions for document management. Collax Document Management offers you a comprehensive solution that optimizes your workflows, standardizes document management and enables cost savings.
Optimized workflows
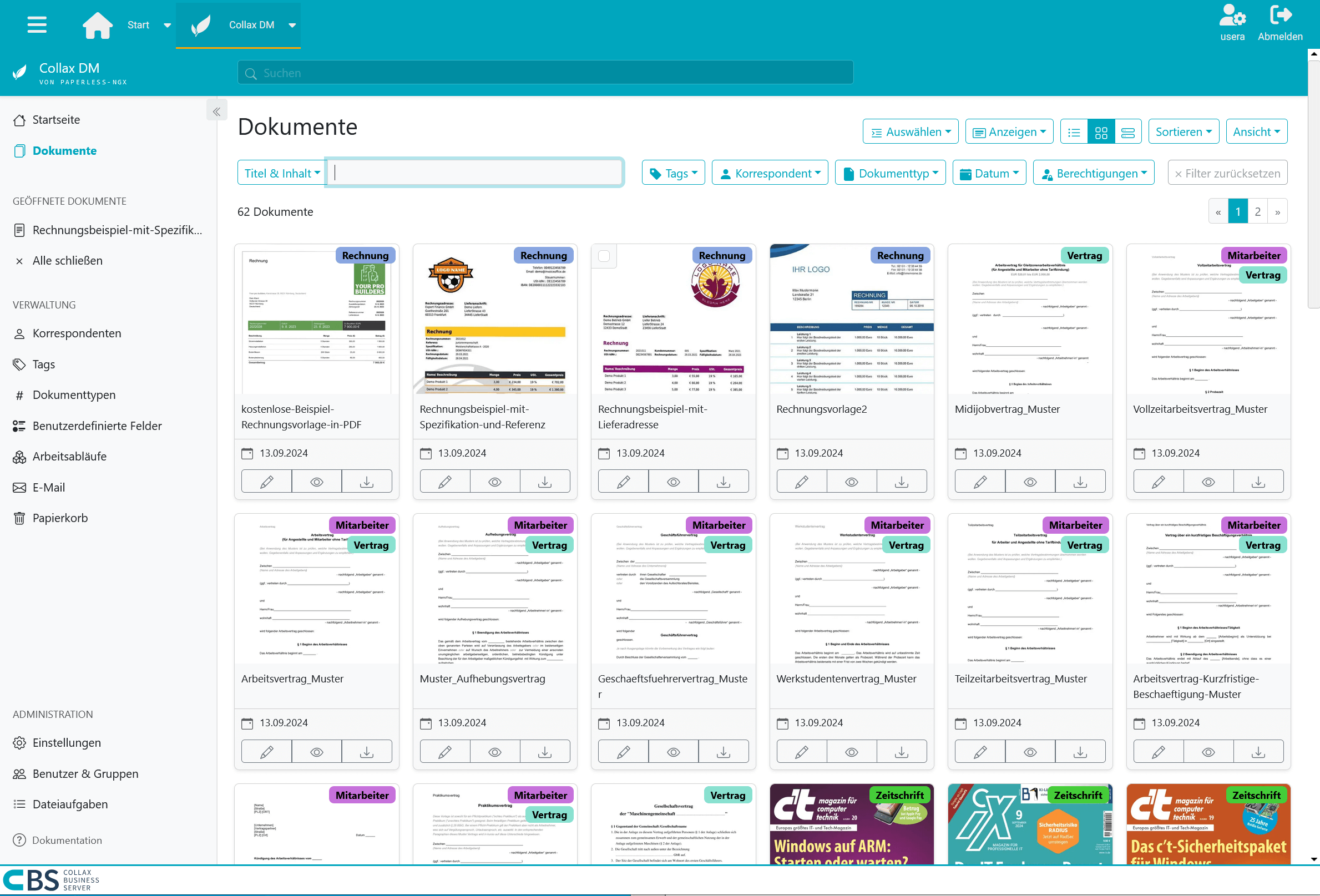
In today’s information overload, it is crucial to be able to access relevant data quickly and efficiently. With Collax Document Management, you can optimize your workflows. The intuitive user interface enables your employees to create, edit and manage documents quickly and easily. Automated processes reduce manual intervention and minimize sources of error. Documents can be found easily at any time. Either because they are immediately accessible via the categorization or because they can be found immediately via the indexed full-text search.
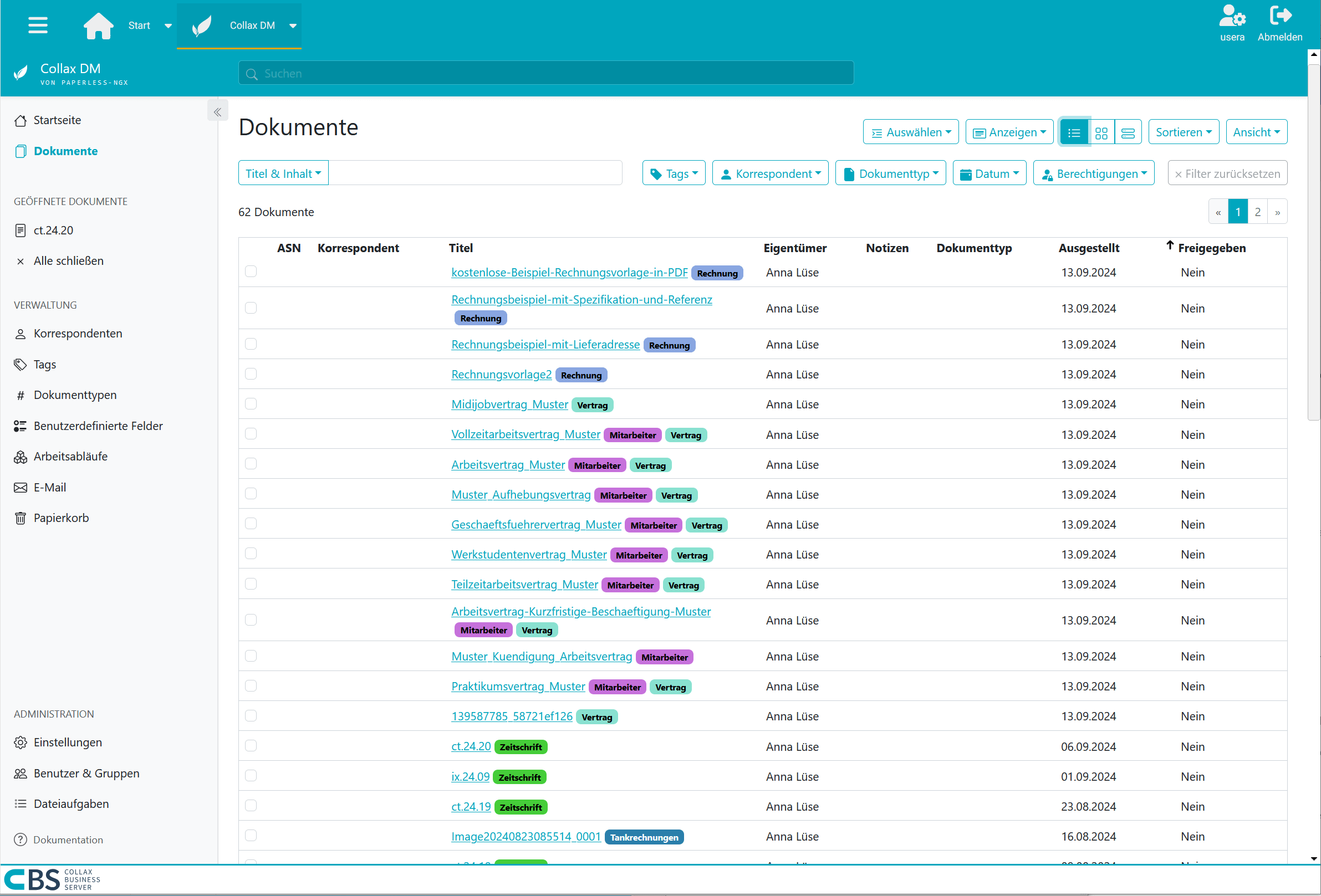
Easy to search, quick to find
The findability of documents is crucial for productive work. With our Paperless-ngx-based solution, you benefit from a powerful indexed search that allows you to find relevant information in seconds. By indexing all documents, keywords and metadata are captured so that search queries can be processed at lightning speed. In addition, a sophisticated categorization of your documents ensures that you can quickly access them not only via search terms, but also via defined categories and folder structures. This combination of indexed search and intelligent categorization ensures that you always have an overview and can access the information you need - whether it’s invoices, journals, contracts, reports or other important documents.
Secure data management
Data security is a top priority. With Paperless-ngx, you benefit from state-of-the-art security standards that protect your sensitive information. Our solution offers encrypted data transmission and multi-level authentication processes to prevent unauthorized access. In addition, regular backups and robust authorization management ensure that your data is secure and available at all times. Rest assured that your information is in the best hands.
Cost savings
The implementation of Collax Document Management not only leads to an improvement in efficiency, but also to considerable cost savings. It is not only the reduction in paper consumption that reduces your operating expenses in the long term. Automated processes also minimize the time spent on administrative tasks, which in turn frees up resources and makes your company more agile.
Precise text recognition
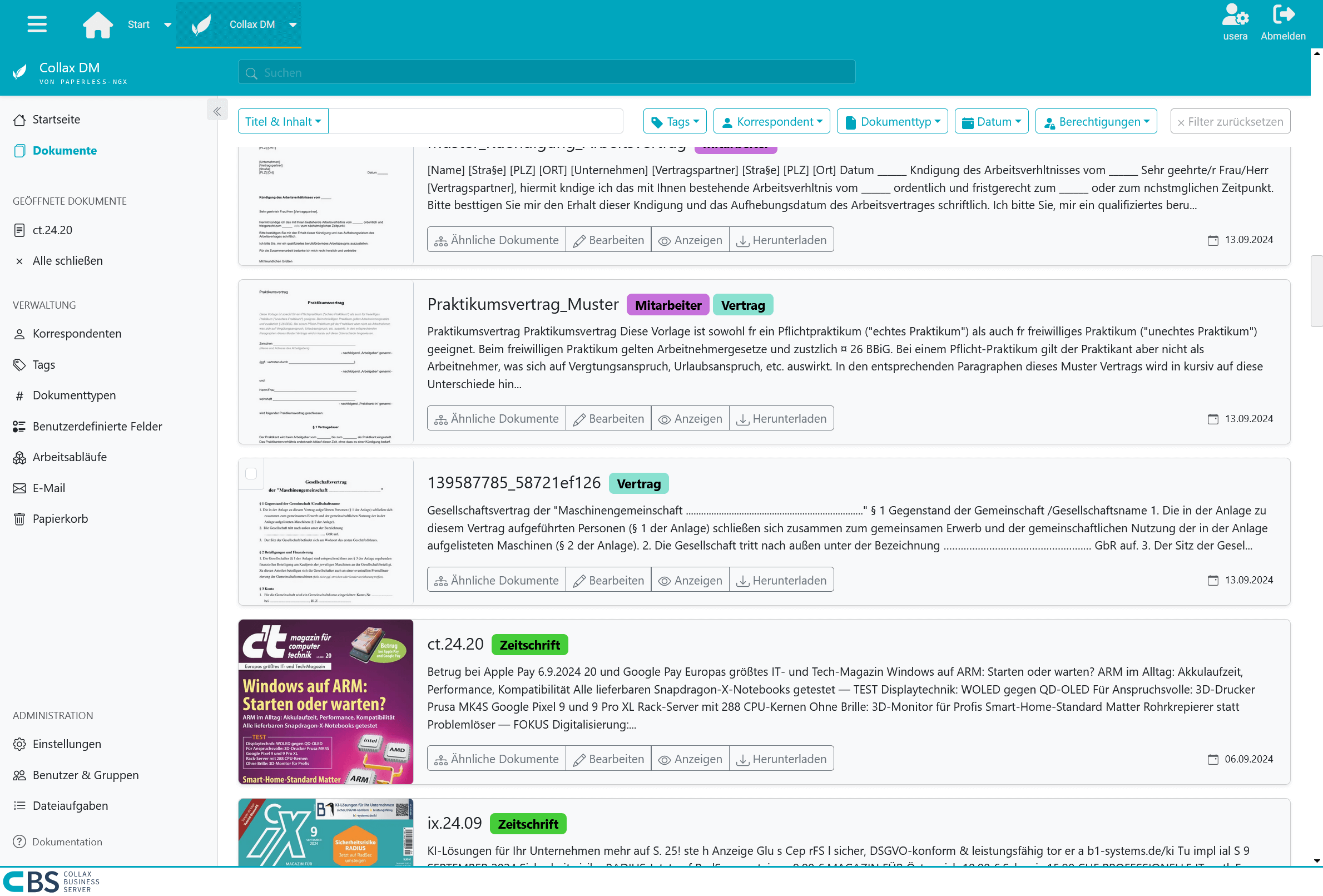
Thanks to the OCR functionality, you can also convert scanned documents and images into searchable text, which significantly improves the retrievability of information. The highlight: a barcode can be attached to the document during scanning for categorization. Automatic text recognition not only saves time searching for specific data, but also increases the productivity of your employees as they can focus on value-adding tasks instead of spending time manually entering or reviewing paper documents.
Easy to get started
If, like us, you start with invoice receipt, you no longer want to do without a document management system. Open and paid invoices can be separated at a glance. Invoices that still arrive by post are stored directly as a document by the scanner and categorized accordingly. The month-end closing is done in no time at all. The tax consultant rarely sends reminders for missing invoices.
Collax Central
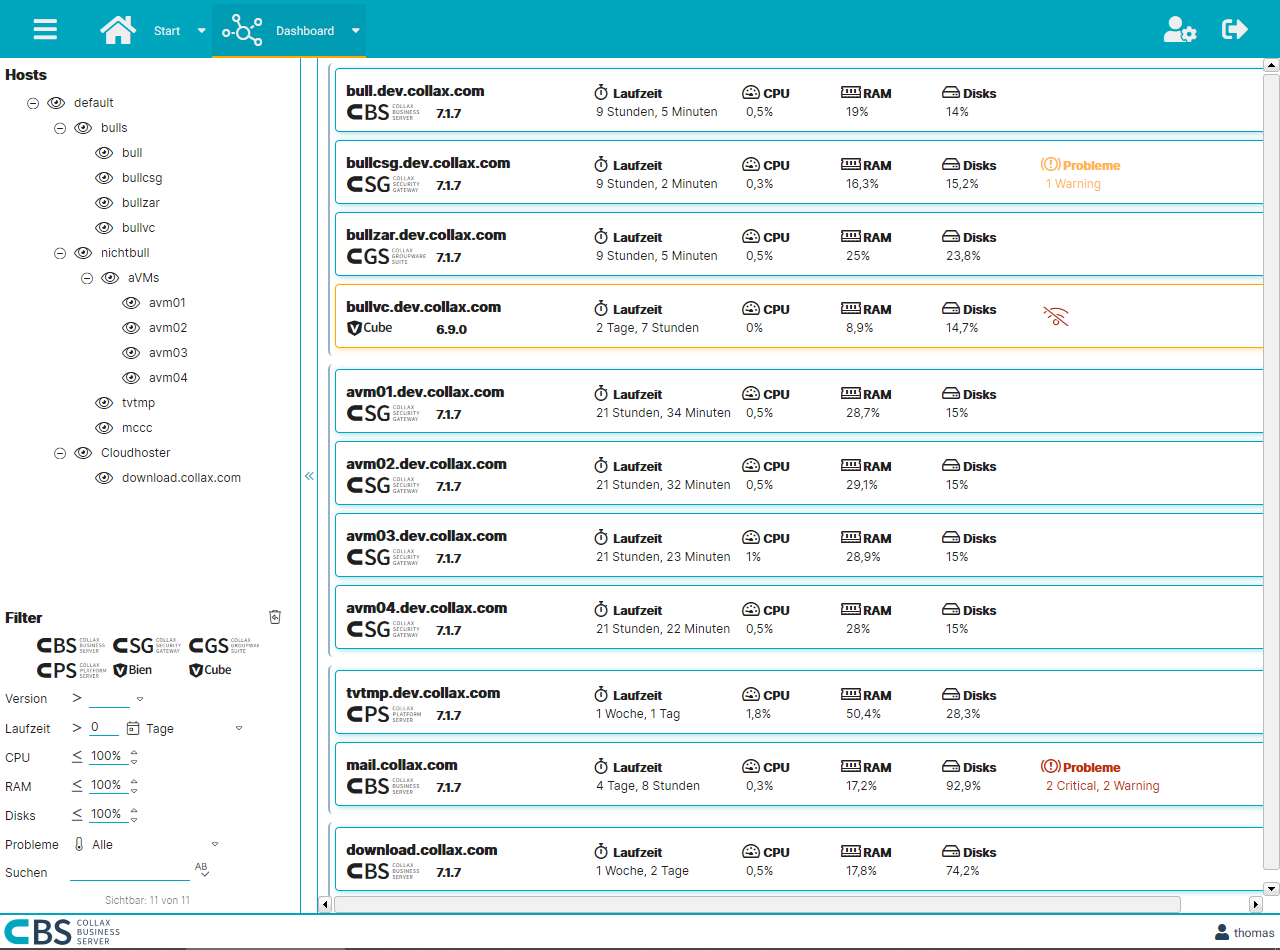
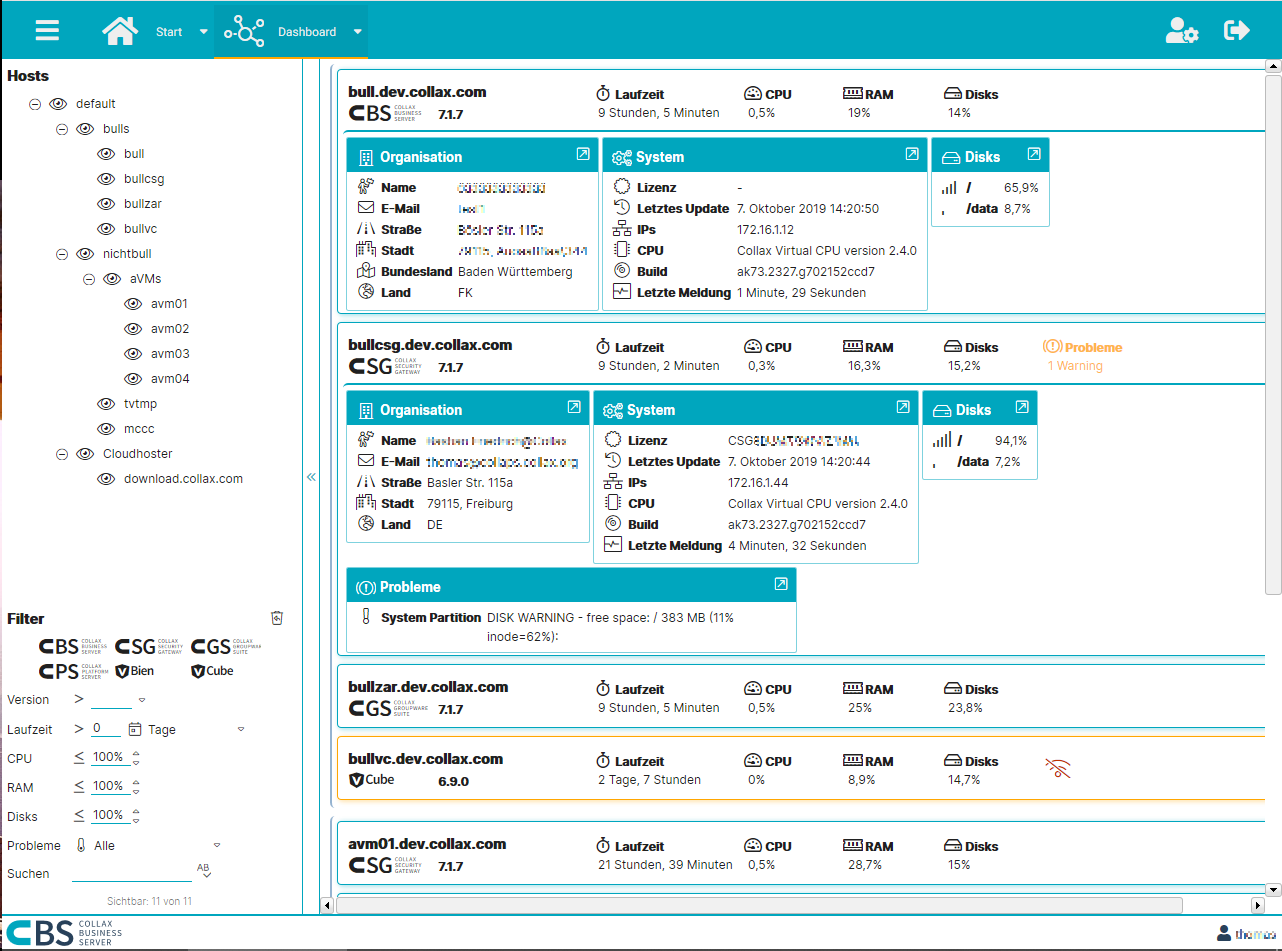
With Collax Central you always have an overview of all Collax servers. This makes administration much easier. Thanks to active system monitoring, Collax Central points out problems at an early stage and offers an effective tool for efficient and fast administration. This is where all the information comes together. This allows problems in a large server landscape to be identified at a glance. Sporadic and regular maintenance tasks are completed quickly.
Always everything in view
The compact overview provides immediate access to all important information on hardware utilization, updates and license terms. Many more detailed information can be displayed with a single click. If maintenance work is due or a problem is detected, a further click is sufficient to perform the administration task.
Hierarchy and structure make the difference
All servers can be sorted into a freely configurable, hierarchical structure. The administrator can create his individual dashboard according to his requirements. Thus he has all information available quickly and clearly. The flexible search function as well as a multitude of filters complete the range of functions.
Collax V-Transfer
The Collax V-Transfer module gives administrators more flexibility in handling VMs and increases scalability when Collax V-Bien, Collax V-Cube and Collax V-Cube+ interact. This is because Collax Transfer provides functions for transferring VMs between the products as required.
Simple and safe operation
With just a few mouse clicks, it is possible to transfer a VM directly between two Collax V-Servers or to change the storage type and other properties before the transfer. Before the transfer starts, a detailed check is performed to determine whether the VM can be operated on the opposite side. Actions that affect the smooth transfer and errors during the transfer are prevented respectively intercepted.
Optimal interaction: Collax V-Transfer and Collax Central
Together with Collax Central, the operation of Collax virtualization solutions is significantly enhanced. A transfer can be initiated conveniently via the dashboard.
- Higher scalability
- More flexibility
- VM transfer between all Collax V products
- Convenient operation via Collax Central
Acronis Cyber Protect - Backup Advanced for Collax Virtualization
Based on Acronis technology, the solution uses efficient disk imaging to provide the industry’s fastest backups and most flexible and reliable recovery options.
Backup can be so fast and easy. Individual files, applications or entire virtual machines can be restored in no time at all - all from one backup. Acronis Cyber Protect - Backup Advanced for Collax Virtualization can restore your data to its original location or to a completely new location.
Functions
- Restoring a Server as a Virtual Machine (VM)
- Backup directly to tape
- Server migration
- Disaster Recovery
- Efficient incremental backups
- Central administration and reporting
- Deduplication
- The world’s leading backup solution
- Multiple awards
- Seamless integration into all Collax V-Servers
- Simple administration - also available remotely
- Transparent cost structure - One license per node (regardless of the number of virtual machines)
- Single Point of Contact: Support about Collax
Collax Advanced Networking
Almost every company depends on a fast and functioning network connection. The module Collax Advanced Networking offers everything needed to keep the network running without restrictions, even at peak times. Important applications can be prioritized via bandwidth management. The Policy Based Routing function and Multi-WAN ensure that all data traffic is optimally distributed among the available connections. The module is rounded off by a intrusion detection and prevention system.
Bandwidth management
Bandwidth management enables applications to use the network bandwidth more efficiently. For modern communication over the Internet, such as VoIP or online meetings, it is important to manage and prioritize bandwidth intelligently.
Policy-Based Routing
A very elegant method of channeling data in a network is offered by policy-based routing. If there are multiple paths for the data to reach a destination, the path can be specified depending on the protocol. The rules can be applied to both forwarded and locally originated connections (e.g., proxy, VPN).
Multi-WAN
Multi-WAN makes it possible to bundle lines and thus establish network connections extremely cost-effectively with high bandwidths. Integrated load balancing ensures load distribution as well as maximum throughput and fail-safety.
Intrusion detection and prevention
Intrusion detection and prevention (IDS: Intrusion Detection System / IDP: Intrusion Prevention System) provides additional security. The system detects malicious attempts to gain unauthorized access. Attackers can be automatically blocked by the firewall even before they can cause any damage.
- Smooth communication even when the Internet connection is busy.
- Bundling of multiple Internet connections
- Structured distribution across multiple Internet connections
- Intrusion prevention
Collax Avira AntiVir
Collax Avira AntiVir is a high-quality and reliable product for protection against viruses and other malware. It is based on the technology of the market-leading anti-virus company Avira.
Collax has perfectly adapted the award-winning and widely used anti-virus software to the Collax C servers. The solution is seamlessly integrated at the click of a mouse and immediately offers maximum protection against threats from the Internet. Collax Avira AntiVir is based on three different mechanisms: E-mail scanner, file scanner and web traffic scanner.
Collax offers the following variants of the proven anti-virus software:
E-mail Scanner with File Scanner
Installed on the Collax Groupware Suite, the Collax Avira AntiVir extension offers protection against unwanted e-mails and malicious content. We seamlessly integrate Avira’s e-mail scanner and file scanner technology into our servers.
Web Traffic Scanner with File Scanner
In a second variant, we offer the Web Traffic Scanner together with the File Scanner as an extension for the Collax Groupware Suite. This allows you to efficiently and easily control Internet usage within your company. At the same time, the file scanner provides more security by checking data that has been manually brought into the company (e.g. via USB sticks or smartphones).
File Scanner
As a third variant, we only offer the file scanner as an extension to the Collax Groupware Suite. This ensures maximum security for all your data. The file scanner reliably identifies and eliminates infected documents.
- Daemon updates without service interruption
- Administrator alert
- Quarantine for unknown archive formats / file formats
- Automatic deletion of infected files
- Real-time scanning of e-mails (with attachments) and web traffic
- Scan of the file cache
- Supports all popular protocols for file sharing, email, and web
- False Positive Control
Collax Virus Protection powered by Bitdefender
Collax Virus Protection is another solution product that we recommend and offer to protect against viruses. It is aimed specifically at small and medium-sized businesses. The solution uses Bitdefender’s market-leading technology. Installed quickly, it provides triple protection for your business:
E-Mail Scanner
The Email Scanner powered by Bitdefender identifies, analyzes and eliminates unwanted emails with malicious content.
Web Traffic Scanner
The Web Traffic Scanner of Collax Virus Protection allows an efficient and meaningful control of Internet usage. The experience and know-how of Bitdefender combined with Collax are a benefit for the security of your company.
File Scanner
The majority of viruses enter the company manually, e.g. via infected files on USB sticks or smartphones. The infected files are then stored on a file server and can spread throughout the company. With a File Scanner you can identify and eliminate such files. Using the Bitdefender File Scanner on a Collax server allows for accurate localization and efficient scanning technology.
Collax offers all three methods either individually or as a complete package.
- Automatic Updates
- Administrator alert
- Quarantine for unknown archive formats / file formats
- Automatic deletion of infected files
- Scan for all common viruses, Trojans and other malicious software
- Real-time scanning of e-mails (with attachments) and web traffic
- Scan of the file cache
- Supports all popular protocols for file sharing, email, and web
Collax Anti Spam powered by Bitdefender
Collax Anti Spam powered by Bitdefender combines multiple spam and phishing detection technologies to detect and block cyber threats in email traffic. Emails are captured and pass through a variety of blacklists, reputation systems and content filtering technologies to detect spam, phishing, extortion scams and malspam attacks, providing complete email protection for internal users and customers.
High detection rate independent of language and region
The spam filter of Collax Anti Spam is characterized by a high detection rate. The detection rate of the solution is not influenced by language. Collax Anti Spam powered by Bitdefender uses information that does not depend on language or regional characteristics; therefore, it provides the same detection rates for users all over the world.
High throughput, high performance
Collax Anti Spam is specifically designed to ensure high throughput without significantly impacting the performance of your systems … for more efficiency in your business.
Protects email servers and collaboration platforms
Accurate spam filtering removes more than 99.9% of unwanted messages and minimizes false positives. By using powerful anti-spam solutions, productivity losses due to spam and unnecessary technical expenses are avoided.
Not only does inbound spam create costs and risks, but outbound email traffic must also be risk-free to prevent your infrastructure from being misused to send spam and viruses. Otherwise, there is a risk that your IP and domains will be blacklisted.
- Protects email servers and collaboration platforms
- Increased employee productivity
- Better protection through cloud-based technologies
- Low false positive rate
- High throughput, high performance
- Real-time email scanning
Collax E-Archiv
Archive for e-mail and e-invoicing
Every taxable company is instructed to archive business-relevant e-mails and e-bills (electronic invoices) in a revision-proof manner. The Collax E-Archive is a simple way to meet the requirements of the Ministry of Finance. In order to facilitate the daily work with e-mails, each employee can be given access to his or her own e-mail archive.
Fast commissioning
The Collax E-Archive can be activated quickly and easily. It archives incoming as well as outgoing emails and e-bills and forwards an unchanged copy to the mail server. This process is automatic and tamper-proof. Archiving can also be performed if the mails are forwarded to another mail server.
One archive for each user
Beyond the obligation, each employee can be granted access to his or her own e-mail archive. A powerful search function makes it possible to conduct extensive searches in old correspondence. Each user can restore e-mails himself. In addition, the archiving ensures a lasting relief of the mail server.
Compliance with legal requirements
The e-mails are indexed before being forwarded to the mail server. This means that the e-mails can be found more quickly later. They also receive a signature so that authenticity and integrity can be checked when they are retrieved. Images for read-only media such as CD, DVD or Blu-ray Disc are automatically generated for long-term, revision-proof storage.
Prevent misuse
If it becomes necessary to search the entire archive, there is an auditor who can access all emails and e-bills. In order to prevent misuse, it is necessary for a second user (e.g. a works council) to confirm full access with a second password according to the four-eyes principle. An e-mail notification to a stored address is triggered. Every search carried out by the auditor is logged by the system.
Legal situation
The ministry of finance has concretized with the principles to the orderly guidance and storage of books, records and documents in electronic form as well as to the access to data (GoBD) how with tax-relevant dates, that were not processed in paper form, must be proceeded. The guideline prescribes a long-term, unchangeable and safe storage of the messages. A conventional archiving as expression excludes it explicitly.
- Audit-proof storage of e-mails and e-bills
- Meets legal requirements
- Four-eyes principle
- Verifiable data integrity (signing of archived e-mails)
- Tamper-proof archive
- Open, platform-independent archive format
- Archive for any e-mail server
- Simple and fast procedure
Kopano Groupware for Collax Server
Topics such as BYOD, file sharing and web meetings are not just buzzwords, but also increasingly dominate the everyday work of small and medium-sized companies. A company-wide available IT platform is essential for business communication.
Groupware on the desktop, in the browser or mobile
The Kopano Groupware offers all the familiar email, advanced calendar and contact features so you can be productive. The browser-based interface gives you an overview of what’s important to you, whether it’s incoming email, your weekly schedule, or the contact details of the person you want to call.
Web-Meetings
Meet online in an incomparable video and audio quality, directly via the groupware WebApp. Use the presentation mode to increase your team’s productivity or simply share your screen so all participants look at the same document.
See who’s online and start an online meeting or chat with just one click.
Invite external participants to your web meeting via e-mail or directly from the meeting request. All you need is a browser to attend your meeting.
File Sharing - Stay in Control
It is easy to share files and folders using your existing storage tools like Collax Net Storage or Owncloud/Nextcloud. With this feature you can browse your folders and keep control of who has access to shared data without switching to another application.
And if someone shares a file or folder with you, you can work on it directly from the WebApp interface.
Mobile access
With smooth synchronization, you always have up-to-date e-mails, tasks and contacts on your smartphone or tablet. Not only can you synchronize your company’s address book, you can also schedule meetings, view your emails or attachments, and reply from your phone. No additional applications required! The Z-Push functionality is also Microsoft Outlook ™ compatible. Outlook 2013 and Outlook 2016 can therefore also be configured to synchronize data via Z-Push.
Restoring individual e-mailsThe Kopano-based brick level Backup / Restore allows you to restore individual e-mails, appointments or mailboxes easily.
- Networked working in a team
- Extended calendar function
- Web meetings in highest video quality
- BYOD - reliable integration of mobile devices
- ActiveSync and Outlook
- Enterprise E-Mail-Server
- Secure file sharing
- Integrated mail server
- Spam and virus protection
- Audit-proof archive for e-mail and e-invoicing
- Location-independent working
| Basic | Pro | |
|---|---|---|
| WebAccess / Webfrontend | ||
| Outlook-Support | ||
| ActiveSync for mobile devices | ||
| IMAP-/POP3-Gateway | ||
| iCal-/CalDAV-Gateway | ||
| Kopano Files Personal | ||
| Multi-User-Calendar | ||
| Brick-Level-Support | ||
| Active Directory-Support | ||
| System Monitoring | ||
| Kopano Webmeetings | 1€ per user / month | |
| Kopano Files for Teams | 0,50 € per user / month |
Collax Let’s Encrypt
Let’s Encrypt is a certificate authority that offers free X.509 certificates for SSL encryption.
The usual manual procedures are replaced by an automated process simplified. The CA of the Let’s-Encrypt certificates is available for all common Web browsers as a pre-installed, trusted root certificate authority deposited. Thus, browsers do not report warnings or errors for web pages that Encrypt HTTPS with a Let’s-Encrypt certificate Let’s Encrypt Certificates are primarily intended for the encryption of web pages. However, you can use can also be used for other purposes.
The goal of Let’s Encrypt is to enable the setup of an HTTPS server which automatically generates a trusted browser certificate without receives human intervention. This is achieved by executing a Certificate Management Agent on the Web server.
For more information, see also: https://letsencrypt.org/de/
- Validierung und Signierung von X.509-Zertifikaten
- Automatische Bereitstellung eines Browserzertifikats
- Zuverlässige Verschlüsselung von Web-Seiten
- Sichere Domain-Validierung
- TLS-Verschlüsselung mit Let’s-Encrypt-Zertifikaten
Collax SSL-VPN
Today, some information from the company network must also be accessible to external employees at all times. SSL-VPN is the best choice if access is to be quick and easy and security plays an important role. Collax SSL VPN provides functions to connect employees to the company network without installing access software. Only a standard browser is required for access. Thus laptops, tablet PCs or smartphones can be used.
Browser desktop
Via a browser applet it is possible to remote control a shared computer. The workstation from the company becomes mobile - it can be operated effortlessly from on the way or from the home office. You can work with mouse and keyboard as usual. Alternatively, it is possible to use the “Remote Desktop Connection” program available under Windows.
Desktop applications
If access to a specific application on an internal server is necessary or desired, Collax SSL-VPN can establish the required network connection. In order to establish the connection, the user only has to log on via browser. The connection between the application and the server is established in the background. The user can now work as in the office without noticing any difference.
Web applications
Web applications are often used in the internal network that only have a low level of security or can be accessed without user logon. Direct access from the Internet is therefore not possible. Collax SSL-VPN enables secure external access to these applications. After authentication, authorized users can use the application in the usual way.
Security
Each tunnel is protected from access by third parties with modern encryption technology. In addition, the administrator can specify exactly which data is released for which employee and via which type of access.
- Secure access to closed networks
- No installation of clients necessary
- Remote access via any browser
- Assignment of user rights per user
Collax Surf Protection
Time-controlled usage control for web shops, social networks or news sites: Control when your employees can access which websites. Collax Surf Protection is based on Cobion’s sophisticated URL database.
- One of the largest URL databases
- One of the largest image databases
- 68 categories, updated daily
- Up to 150,000 new URLs daily
- Real-time adjustment (Real-Time Monitoring)
- Can be used as blacklist or whitelist